A lot has been written lately about passwords, and about big hacks on websites that have revealed passwords. I won’t link out to them because the problem isn’t going anywhere and there will be a fresh batch before you know it!
There are a lot of different points of view about what a password should look like and contain. The general consensus is that they should contain upper and lower case, numbers and special characters, and the same password should not be used across all websites. There should be a segregation of passwords across types of website; banking and news site passwords should be very different.
Once you get past signing in to a couple of websites things have got pretty unmanageable, especially as each one has its own rules about what sort of characters you can have in that password. How do you remember which password belongs to that site? Normally this question isn’t answered. The best thing that I have read on the subject is Password Security: Why the horse battery staple is not correct [^] – head over and read it, I’ll wait. In that article, Diogo Mónica says that our passwords should be unique and strong, but we should not be trying to remember all of them.
This is a solved problem, we should be using a password manager instead. Put a good strong password on the file and encrypt it, and remember that one password, then no-one except you can get to those passwords. There is usually space to store other details for each sign-on as well, like the email address or mobile number that you used when you created the account. Another good thing about password managers is that they will generate strong passwords for you based on the selectable criteria – upper and lower case, spaces, numbers, special characters and length. Once you have tried a password manager you won’t want to go back to the way you are doing it now.
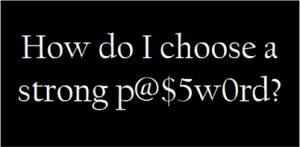
There are password managers for all of the operating systems that you are likely to be using, and some integrate into your browser as well. If you are using many devices (computer, laptop, mobile, tablet …) combine the password manager with a free online syncing service like Dropbox (Referral Link, help me earn more free space) [^], then all of your passwords are up-to-date and available all of the time.
Links:


The hobby is dying …
It interesting sitting across multiple hobbies / interests and seeing the parallels and difference. In this case dog showing and railway modelling. Both have their fair share of deep thinkers
Mike at OST Publications, one of the model railroaders who seems to look at things in a different light, just blogged this:
Sorry Mike, you had already boiled that post down to the absolute essence of the matter, there’s no room to just skim a morsel out of it!
Could this possibly apply to dog showing? Of course it can, we hear enough of the crisis mode not too much of the “opportunities” mode. We were helped and encouraged into the community and hope that we can do the same.